no-effaceable-storage
Dual booted OS is almost ready to boot, we just need to generate a keybag or copy it.
Copying is the best option. However, you won’t be able to set a passcode. If you set one on a system with copied keybags, effaceable keys will be regenerated and first OS won’t boot anymore. (Then you’ll need to restore the device).
cp -av /var/keybags /mnt2
Generating should only be used if main OS keybags are not compatible with secondary system. Most of the time if SEP is compatible, keybags from the main OS will also be compatible.
This process is also very dangerous on A10+ devices. Generating on the iPhone 8 seemed not to work at all, and required a restore.
However, if you choose to generate it, continue here.
Patching devicetree
I wrote a patcher to automate the process. Unpack devicetree:
img4 -i DeviceTree* -o dtree.raw
Patch it:dtree_patcher dtree.raw dtree.patched -n
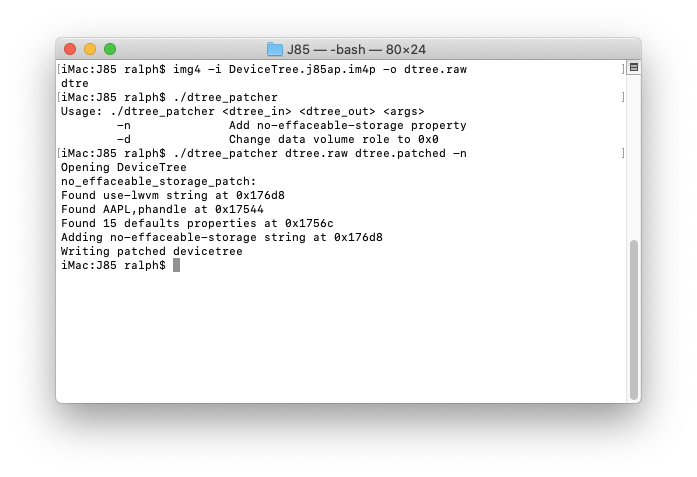 And pack patched devicetree into img4:
And pack patched devicetree into img4:
img4 -i dtree.patched -o devicetree.img4 -M IM4M -A -T rdtr
Adding fixkeybag
Thanks to @nyan_satan for this technique. We’ll make our keybag generate when booting for first time: compile fixkeybag for arm64 and put it in / of disk0s1s3 (don’t forget to sign it using ldid for iOS 10, ldid2 for iOS 11+). Save original keybagd, sign fixkeybag and replace it with fixkeybag
mv /mnt1/usr/libexec/keybagd /mnt1/usr/libexec/keybagd_bak
mv /mnt1/fixkeybag /mnt1/usr/libexec/com.apple.keybagd
ldid -S /mnt1/usr/libexec/com.apple.keybagd
mv /mnt1/usr/libexec/com.apple.keybagd /mnt1/usr/libexec/keybagd
Second system is ready to boot. Now we have to patch bootchain and boot it.